Retire Legacy Applications While Retaining Data Accessibility
- By:
- Bill Tolson |
- August 18, 2020 |
- minute read
As the move to the cloud and cloud-based applications continues, organizations are assessing the real costs of maintaining legacy applications. As a result, on-premises legacy application retirement has now become a goal of many corporate IT organizations for several reasons, including:
- Cost reduction – reallocating or decommissioning of the hardware/software as well as the personnel to manage them can provide measurable cost savings
- Application consolidation – many corporate applications have become redundant over time, especially where one company has purchased another
- Regulatory compliance – heightened levels of regulatory compliance is forcing Chief Regulatory Officers and Records Managers to get a better handle on all data
- Litigation/eDiscovery – responding to an eDiscovery request means finding and turning over all potentially responsive data. Data in legacy applications, or orphaned data, drive up the cost of eDiscovery
- Risk reduction – GDPR/CCPA privacy regulations have focused more attention on legacy application/orphaned data, i.e., the right to be forgotten. If requested PII is not found and deleted, the risk of fines is increased. Plus, as mentioned above, responding to an eDiscovery request requires ALL potentially relevant data must be found and turned over. If data sitting in legacy application repositories are not found, costly eDiscovery sanctions or an adverse inference are sure to follow.
For this blog, I will concentrate on two of the above topics; regulatory compliance and eDiscovery (both include risk mitigation.)
Digital Transformation and Legacy Application Retirement
Digital transformation has been a hot topic for several years. The basis of digital transformation is to use technology to transform your company's business into something significantly better. The cloud has become a major enabler for digital transformation. The cloud provides companies the ability to scale their IT needs better, realize higher levels of security, and deliver better employee data access. All of which have becoming increasingly important, thanks to the current COVID-19 pandemic.
As more companies move forward with their digital transformation, the challenge of what to do with long-held legacy applications becomes more of an issue. Additionally, companies face the question of what to do with legacy application data. In the past, organizations would either:
- delete all legacy application data so they could decommission the applications, or
- they would keep the legacy application active to meet eDiscovery and regulatory requirements.
eDiscovery and Legacy Application Retirement
Let me state upfront; organizations are under no obligation to save all corporate data forever in case litigation arises sometime in the future. However, if future litigation can be reasonably anticipated, then companies have a responsibility to protect all potentially relevant data, including data associated with legacy applications. A mistake many companies retiring legacy applications make is not preserving access to orphaned application data, especially if that data cannot be searched and viewed without the availability of the original legacy application.
Historically, companies have either decommissioned the application and deleted all associated data – a risk if possible litigation is evident in the near future. This action will be seen as a possible destruction of evidence (spoliation) and could cause case loss.
Or, they have decommissioned the application and left the data in storage limbo. This strategy causes other expensive problems. Retiring a business application without addressing its associated data can leave you with vast amounts of orphaned data that can become a costly problem later. If the opposing counsel has reason to believe that relevant data could exist in the legacy application's dataset, the defendant may be forced into reinstalling the application (assuming that’s even possible), paying for needed equipment and application upgrades, and employing consultants to reconfigure and search the legacy app for relevant data to satisfy the eDiscovery request.
The first strategy - data deletion - is risky if the company should have anticipated a future lawsuit that could involve the deleted data. The second strategy could be expensive as well as cause the company to fail to meet eDiscovery timeframe parameters.
READ MORE: Data Has Value, but also Risk – Get Rid of What You No Longer Need
Regulatory Compliance and Legacy Application Retirement
Regulatory compliance is the act of making sure an organization is following the laws that are relevant to its operations. Almost all industries have some form of industry or government compliance requirements. To comply, a company is required to perform certain obligations, i.e., data retention, to comply with existing laws/regulations.
For many reading this blog, regulatory compliance means ensuring certain types of data are captured, retained, managed, provided to regulators when asked, and now with the new privacy regulations, securely disposed of if requested.
Legacy applications and application retirement can complicate regulatory compliance in several ways:
Regulated records may be present in a legacy application. If all data is deleted when the application is retired, compliance-related records could be lost – causing the company to be "out of compliance," which could mean a hefty fine, litigation, and loss of business.
On the other hand, if the application data is orphaned (after the legacy application is decommissioned), access to the regulated data could be deemed impossible, or at a minimum, very expensive to recover.
Another recent development with legacy application retirement is the extensive data management requirements for new and emerging privacy regulations.
In a May 2018 research report titled “How to Address Data Retention and Application Retirement” (report # G00355820), Gartner estimated that by 2022, 80% of organizations affected by the General Data Protection Regulation (GDPR) that do not engage in application retirement would be fined for non-compliance. The same issue would also apply to CCPA compliance, greatly expanding the number of affected companies.
Privacy Regulations Still Govern Orphaned Data
The new privacy regulations impose strict security requirements on not only data but also data management requirements. This is so companies can quickly respond to data-subject PII information requests, including which PII is being held, how it's being used, and if it’s been sold and to whom. Additionally, data subjects have the right to demand the deletion of all their PII.
Now suppose a data-subject contacts your company and asks for information on what PII your company has on them. Your company must search all databases, file shares, email repositories, and other application systems (such as CRM) that could contain their PII. The privacy laws leave little wiggle room in the searching and reporting of target PII. The main requirement is that all applications and repositories must be searched for that data subject’s PII. What if a legacy application had been neglected over the years and had reached the point of being unusable? In this scenario, the company might incur significant costs bringing the application and data back to a state where it can be queried.
Another example of legacy application risk is where a legacy application was decommissioned (deleted) while leaving the data intact but orphaned, without an app that can read the data. Again, the company would be forced to spend a bunch of hiring consultants and purchasing new hardware and software to make the orphaned data searchable again. A common argument to solve the problem of orphaned application data is to simply delete all legacy application data once the application is decommissioned. If the dataset doesn't exist, then it cannot contain any PII. However, this ignores the need to keep compliance-related data.
READ MORE: Cyberhackers are Targeting your Organization’s Sensitive Data
Legacy Application Retirement and Data Archiving
The best practice for legacy application retirement is to archive the legacy datasets into a cloud archive, which includes the ability to intelligently recognize, read, and manage (retention/disposition) the legacy application's data formats – before the legacy application is decommissioned.
The benefits of this approach is that it ensures continuous access to retired application data for regulatory and eDiscovery purposes, delivers the costs savings you’re trying to achieve by decommissioning costly legacy applications, and supports your company’s digital transformation strategy. A cloud-based archive will also provide a secure repository to consolidate all your legacy application data for ongoing analytics and information management.
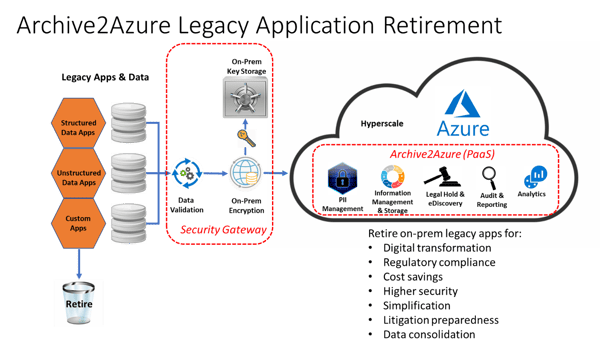
Figure 1: The Archive2Azure Information Management and Archiving Cloud platform is the only cloud-based PaaS platform that provides a secure repository for all your legacy application data
Archive2Azure Information Management and Archiving
Archive360's Archive2Azure PaaS platform is a complete cloud-based information management and archiving solution for both structured and unstructured data, which is installed in your company’s own Azure Cloud tenancy for increased security and functionality, ongoing customization and complete control. Unlike SaaS cloud platforms where you are forced into a one-size-fits-all application and security configuration, the Archive2Azure PaaS solution is architected so that you store your company's data in your own Azure tenancy with complete control over the security, including the ability to encrypt data on-premises before movement to your Azure tenancy – while keeping your encryption keys locally.
Bill is the Vice President of Global Compliance for Archive360. Bill brings more than 29 years of experience with multinational corporations and technology start-ups, including 19-plus years in the archiving, information governance, and eDiscovery markets. Bill is a frequent speaker at legal and information governance industry events and has authored numerous eBooks, articles and blogs.