Data Privacy & Security: Top Business Drivers for InfoGov
- By:
- Bill Tolson |
- July 27, 2022 |
- minute read
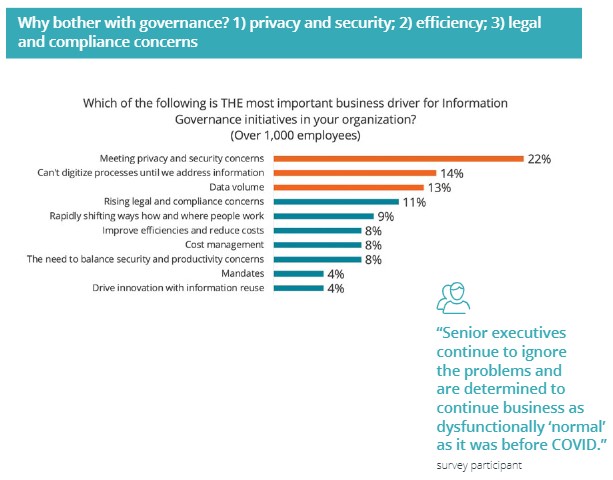
According to a recent 2022 survey published by the MER organization, the number one business driver for information governance initiatives is data security. Specifically, ensuring enterprise data security is good enough to ensure compliant data privacy.
But why have data security and data privacy suddenly become the top priority for information governance initiatives?
New data privacy laws drive new data security initiatives for information governance
There's little argument that the single biggest driver for this new information governance focus is the rise of cybercrime that has caused citizens to demand new, more protective data privacy laws from their federal, state, and local governments. Additionally, corporations around the world are waking up to the rising financial risk that new data privacy laws pose if they do not take seriously information security of, particularly for sensitive data.
The current state of data privacy began with the emergence of the EU's GDPR data privacy law. One of the most significant concepts introduced with the GDPR was the statement that data privacy was a human right. Since the advent of the GDPR, many countries around the world have introduced their own data privacy laws governing how their citizen's personally identifiable information (PII) is treated.

Webinar Replay: The Impact of Privacy Regulations on Businesses
The impact on enterprises is significant. Instead of PII serving as a corporate resource that a company can use for sales, marketing, and analytics in perpetuity, companies across the globe are now being forced to treat the personal data they collect as a valuable asset owned by the individual data subjects and held in trust by the organizations they have permitted to collect, maintain, and use it – but only in the specific manner approved by the data subject.
The growing number of new privacy laws hit AdTech companies and Data Brokers the hardest. However, any organization with substantial collections of customer data will be forced to make significant changes to their PII data collection and use practices. This is particularly true for large firms within financial services, healthcare and life sciences, manufacturing, retail, and utilities.
This fact brings us back to the original point from the MER survey that the number one driver for information governance initiatives is ensuring enterprise data security is good enough to ensure compliant data privacy.
You can't protect what you don't know you have
Information governance professionals have a long history of recognizing, capturing, and managing corporate records. These records usually comprise approximately 5% to 10% of all data within an enterprise. However, sensitive personally identifiable information (PII) can be present in all kinds of work documents. For example, in marketing and sales spreadsheets, a presentation discussing user behavior, or correspondence from potential customers. Because these work files are not considered "records" in the traditional records management sense, they are often not actively managed. They are usually scattered across the enterprise (in file systems, SharePoint accounts, OneDrive cloud accounts, email systems, laptops, and external storage), controlled by individual employees, with little or no visibility by IT or other departments.
The new privacy laws have numerous hard and fast rights for data subjects and specific response requirements for organizations when queried by data subjects. The biggest privacy challenge for companies will be how they can respond to a data subject access request (DSAR) if data that could contain the target PII is not centrally managed.
The solution is straightforward – all corporate data must be actively managed and protected in case some contain PII.
[Deciding what data you MUST retain? Read Data Has Value, but also Risk – Get Rid of What You No Longer Need ]
This point brings us back (again) to why data security and privacy have risen to the top of the priorities list for information governance initiatives. Information governance professionals will soon be faced with managing a great deal more data, with a significant percentage of it containing sensitive PII. These new and massive data stores will need to be searchable for DSAR response (requiring them to be indexed), managed for retention and disposition, and secured with higher network and data security levels.
A little-known provision of all the data privacy laws is the requirement to delete PII as soon as its original reason for collection is met. Organizations will no longer be able to keep PII for other uses indefinitely. Additionally, the right to deletion present in all US State bills and laws require data collectors to delete all PII when requested by a data subject.
All these new PII handling provisions, the Information Governance Department will need to be closely involved with both IT and Security teams to ensure information management systems and security protocols are not overly burdensome but still fully compliant to ensure ongoing information governance practices.
The new data privacy/data security landscape
With the continuing rise of cyber-attacks, including ransomware attacks and the new versions of extortionware, more data will need to be protected in more far-reaching and complex ways. The more recent forms of ransomware and extortionware are now exfiltrating (stealing) sensitive corporate data before encrypting the data. The hacker then threatens to release the data (if the ransom is not paid) on the internet to embarrass the company further. The hackers sometimes also contact the individual data subjects to extort further ransom payments.
[ wondering how to protect your organization? Read this blog on How to ransomware-proof your cloud-based data backups, archives, and information management repositories ]
However, with the new data privacy laws and the associated potential penalties and fines, hacked organizations could also face massive fines for allowing PII under their control to be breached and stolen. This issue is driving the new focus on not just enterprise and perimeter security but also on individual file and even field-level data security.
Hackers have become highly successful in breaking through perimeter security using sophisticated phishing schemes which, once in, provide access to large amounts of potentially sensitive data. Thankfully, advanced technologies now exist where individual files (and specific data within those files) can be individually secured with encryption with role-based access controls (RBAC) and zero trust (least privilege) architectures that demand continuous re-authorizations to access sensitive data. These new security technologies and processes are becoming the new norm that information governance professionals will need to understand and navigate every day.
Taking security into your own hands – the power of PaaS
A proven method to up your cloud security posture is to utilize a PaaS-based cloud platform. In a PaaS environment, the customer deploys the solution in their own dedicated deployment infrastructure. There are no shared network resources and no shared secrets between other customers. In reality, PaaS is a ready-to-use cloud platform in which the customer provides their own software and additional enhanced security, instead of a SaaS “shared - one size fits all” security capability. The third-party provides a ready-made, dedicated cloud tenant and specialized software to address a specific software need.
CISOs are now starting to demand Zero Trust cloud architectures before they move their sensitive data to the cloud. With a PaaS model, customer information is stored in the customer’s cloud tenancy (versus the SaaS model which uses a shared tenancy), giving customers the ability to audit their infrastructure and data. Most SaaS solutions are considered a black box: while customers can audit at any time, they usually have no input into the security processes such as encryption key generation, they can’t tell when the SaaS vendor has accessed their data, and their data can be decrypted and turned over to the government using secrecy warrants (which direct the SaaS provider to not inform the customer that their data has been copied).
Another important security aspect is the question of how system updates are installed when the cloud platform architecture is updated. In the case of a SaaS solution, the SaaS vendor controls when an update is done and uses common deployment pipelines to update all customers. As a SaaS customer, you have zero input or control on change management and specific security configurations. In a PaaS model, updates are directly controlled by the customer. Key to security during the update process is that, in addition to owning dedicated security certificates and dedicated network layers, you also utilize continuous integration continuous deployment (CI/CD) pipelines that are specific to you.
These are just some of the measure that enable you to create an isolated/secure enclave. A PaaS solution with a Zero Trust security model ensures the customer controls everything – and there is complete transparency.
With a PaaS cloud platform, you rely on the cloud provider’s security, such as Microsoft’s Azure Cloud or Amazon’s AWS. Both cloud providers offer the highest levels of infrastructure security; however, with a PaaS tenancy, the customer can also add additional data security capabilities such as encryption before the data is moved into the cloud as well as on-premises storage of the encryption keys.
The Archive360 PaaS Zero Trust security platform
Archive360 offers a Zero Trust PaaS-based intelligent information management and archiving platform installed in the customer's own Azure or AWS tenancy providing complete control and ownership of their data. With Archive2Azure and the customer’s Azure or AWS tenancy, the customer can implement additional levels of security including fully private, isolated enclaves. Unlike the SaaS shared cloud model, the Archive2Azure cloud Platform is able to support and be a part of Zero Trust security architecture, i.e., a private/secure enclave, to ensure there are no shared resources, shared encryption keys, or common security certificates.
To reiterate, Zero Trust security is impossible in SaaS clouds.
Additionally, Archive360 offers the Cloud Security Gateway which offers encryption of all data before movement to the cloud, on-premises encryption key storage, access controls, and homomorphic and field-level encryption for total data security in transit, at rest, and WHILE IN USE.
My next blog will focus on how the transition to the cloud has spurred new cloud security best practices to better ensure that the PII subject to these new privacy laws is not lost to cyber thieves.
For more information on the emerging data privacy laws and new data security requirements, please contact the experts at Archive360 by emailing us at info@archive360.com or calling us at +1 (212) 731-2438.
Bill is the Vice President of Global Compliance for Archive360. Bill brings more than 29 years of experience with multinational corporations and technology start-ups, including 19-plus years in the archiving, information governance, and eDiscovery markets. Bill is a frequent speaker at legal and information governance industry events and has authored numerous eBooks, articles and blogs.